You can also write custom scripts to sign the executable using a PFX file, a token-based certificate, or a certificate stored in an HSM (Hardware Security Module).
This option gives you full control over the signing process and supports dynamic parameters (making your script reusable with different inputs).
-
Create a .cmd file (e.g., sign_app.cmd) and place your signing logic into this file.
-
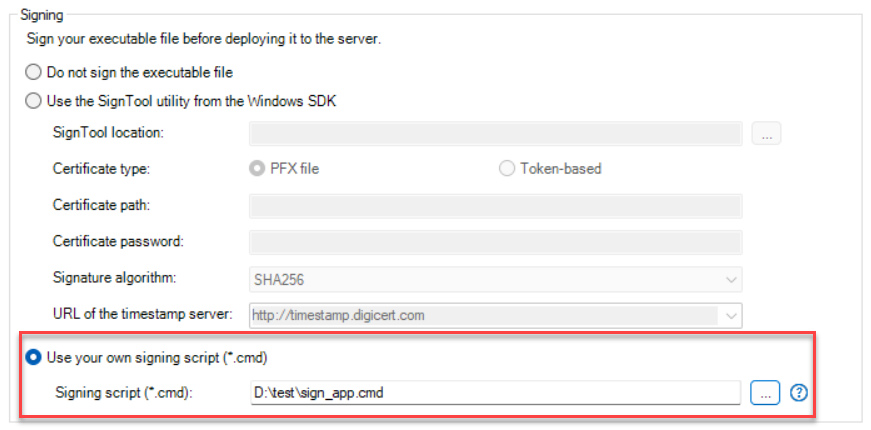
In the PowerServer project painter > Security page, select "Use your own signing script", and then set the script file path to the .cmd file.
If signing with dynamic parameters, you must also pass in the parameter values immediately after the file path of the .cmd file.
Examples
The following examples demonstrate how to use a PFX file and a token-based certificate with both static and dynamic parameters.
To sign with a PFX file,
-
To sign with a PFX file with static parameters, you may write the following scripts in the .cmd file (using Microsoft’s SignTool for example):
signtool.exe sign /f mycert.pfx /p password /d "My application" /du http://www.mytest.com /fd sha256 /tr "http://timestamp.digicert.com" /td sha256 salesdemo_cloud.exe
-
To sign with a PFX file with dynamic parameters, you may write the following scripts in the .cmd file:
%4 sign /f %5 /p %2 /d "My application" /du test /fd sha256 /tr %3 /td sha256 %1
And then provide the parameter values right after the file path of the .cmd file:
"D:\test\sign_app.cmd" "salesdemo_cloud.exe" "password" "http://timestamp.digicert.com" "D:\test\signcode.exe" "D:\test\mycert.pfx"
Parameter mapping:
%1: Application executable file name, for example, "salesdemo_cloud.exe"
%2: Certificate password
%3: URL of the timestamp server
%4: Path to the code signing tool
%5: Path to the digital certificate
To sign with a token-based certificate, such as an EV (Extended Validation) code signing certificate,
-
To sign with a token-based certificate with static parameters, you may write the following scripts in the .cmd file:
signcode.exe sign /fd SHA256 /a /sha1 "13731a37233bbd83eeb13e95c7898d1d76a2256c" /tr http://timestamp.digicert.com "salesdemo_cloud.exe"
-
To sign with a token-based certificate with dynamic parameters, you may write the following scripts in the .cmd file:
%1 sign /a /fd sha256 /sha1 %2 /tr %3 /td sha256 %4
And then provide the parameter values right after the .cmd file:
"D:\test\test_token_param.cmd" "D:\test\signcode.exe" "13731a37233bbd83eeb13e95c7898d1d76a2256c" "http://timestamp.digicert.com" "salesdemo_cloud.exe"
Parameter mapping:
%1: Path to the code signing tool
%2: Certificate thumbprint. You are required to specify the certificate thumbprint only if you have multiple certificates.
%3: URL of the timestamp server
%4: Application executable file name
To avoid repeatedly entering the UKey password (for instance the screen is locked or the system is restarted), you can specify the token password in the signing commands, for example:
-
To sign with static parameters, you may write the following scripts in the .cmd file:
"D:\test_newsign\signcode.exe" sign /fd SHA256 /a /sha1 "13731a37233bbd83eeb13e95c7898d1d76a2256c" /tr http://timestamp.digicert.com /td SHA256 -f "D:\test_newsign\cersign.cer" /csp "eToken Base Cryptographic Provider" /K "[{{a*****}}]=p11#f408f337487afa2d" "echarts_cloud.exe"-
-f: Specifies the .cer certificate file exported from an EV code signing certificate
-
/csp: Specifies the cryptographic service provider (CSP) that contains the private key container
-
/K: Specifies the token password and private key container name in this format: "[{{TokenPasswordHere}}]=KeyContainerNameHere"
-
-
To sign with dynamic parameters, you may write the following scripts in the .cmd file:
%1 sign /a /fd sha256 /sha1 %2 /tr %3 /td sha256 /f %4 /csp %5 /K "[{{%6}}]=%7" %8And then provide the parameter values right after the .cmd file:
"D:\EV_code_sign\ev_sign_dyn.cmd" "D:\EV_code_sign\signtool.exe" "725c43e53497a2c13e59682a2c4168f3b2016c76" "http://timestamp.digicert.com" "D:\EV_code_sign\EV_Cer\AppeonInc.cer" "eToken Base Cryptographic Provider" "a*****" "p11#e0c9d4175dd7b020" "echarts_cloud.exe"
Parameter mapping:
%1: Path to the code signing tool
%2: Certificate thumbprint. You are required to specify the certificate thumbprint only if you have multiple certificates.
%3: URL of the timestamp server
%4: The .cer certificate file exported from an EV code signing certificate
%5: The cryptographic service provider (CSP) that contains the private key container
%6: The token password
%7: The private key container name
%8: Application executable file name
Best practices
-
For .cmd files with static parameters, both the file name and directory path can contain spaces.
-
For .cmd files with dynamic parameters, the directory path should not contain spaces, though the file name can.
-
Use absolute paths to avoid path resolution issues.
-
Wrap any path with spaces in double quotes.
-
You can test your script independently in Command Prompt or PowerShell before using it in PowerBuilder.