You can generate your own certificates, and create a Kubernetes secret for use with the ingress route.
For testing purpose, you can generate a self-signed certificate with openssl. For production use, you should request a trusted, signed certificate through a provider or your own certificate authority (CA).
In this guide, we assume that you have already generated a TLS certificate and a private key.
Now, you will generate a Kubernetes TLS secret using the TLS certificate and the private key.
To allow Kubernetes to use the TLS certificate and private key for the ingress controller, you create and use a Secret.
The secret is defined once, and will be referenced later when you define ingress routes.
Step 1: Copy the certificate and the private key to the local publish directory, for example, C:\cloudappdemo\publish.
Step 2: Create a secret. For example, the following command creates a secret named aks-ingress-tls-appeon.com.
kubectl create secret tls aks-ingress-tls-appeon.com \
--key server.key \
--cert server_appeon.com_ssl.cer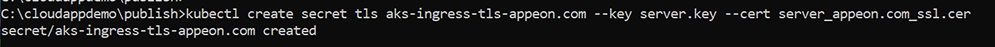
You can also add a default certificate, so that it displays no matter when the IP address or domain name is accessed.
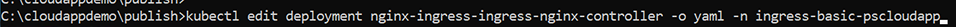
Step 1: Edit the Nginx-Ingress deployment configuration file. For example,
kubectl edit deployment nginx-ingress-ingress-nginx-controller -o yaml -n ingress-basic-pscloudapp
Step 2: Add the following parameter to the configuration.
- --default-ssl-certificate=default/aks-ingress-tls-appeon.com