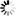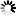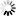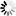PowerBuilder 2025 R2 enhances runtime security by introducing features that protect against DLL hijacking and allow developers to control how DLLs are located and validated on the client machine.
The following options are added to the Security tab of the native client/server, PowerClient, and PowerServer project painter:
-
Strict mode option
The Strict mode option limits the DLL search scope strictly to the defined paths, preventing unauthorized or unexpected DLLs from being loaded.
-
For PowerClient/PowerServer projects, the developer can specify the path of the third-party DLLs in the Third-party DLL loading scope > Strict mode section, so that the application loads the third-party DLLs from the specified paths only on the client machine.
There is no need to input the runtime DLL path, because the runtime DLLs will be automatically loaded from the directory according to the runtime version, for example, %localappdata%\PBApps\Applications\Runtime\25.0.0.3599. PowerBuilder will search this folder automatically before searching the path(s) in the order listed under Strict mode.
-
For native client/server Application projects, the developer can specify the path of the DLLs (runtime DLLs and third-party DLLs) in the DLL loading scope > Strict mode section, so that the application (to be specific, the pcode executable) loads DLLs from the specified paths only on the client machine.
If runtime DLLs and third-party DLLs are located in different folders, you should input multiple paths (separated with semicolons).
-
-
Enable DLL signature verification option
When enabled, PowerBuilder verifies the digital signature of DLLs during application startup. Note: only Appeon-signed DLLs will be verified.
For more information, refer to the section called “DLL secure loading (using Strict Mode)” in Application Techniques.