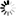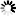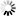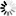Description
Specifies that data should be encrypted before sending it over the network.
When to specify Encrypt
You must specify the Encrypt parameter before connecting to the database.
Applies to
SNC SQL Native Client for Microsoft SQL Server
MSOLEDBSQL Microsoft OLE DB Driver for Microsoft SQL Server
ADO.NET provider for Microsoft SQL Server
Syntax
Encrypt=value
|
Parameter |
Description |
|---|---|
|
value |
Specifies whether data should be encrypted. Values vary according to the driver. For SNC SQL Native Client and Microsoft OLE DB Driver (MSOLEDBSQL 18.x):
For Microsoft OLE DB Driver (MSOLEDBSQL 19.x):
For ADO.NET provider for Microsoft SQL Server:
|
Default value
Encrypt=0 or Encrypt="False"
Usage
SQL Server 2005 always encrypts network packets associated with logging in to the server. If no certificate is provided on the server when it starts up, SQL Server generates a self-signed certificate that is used to encrypt login packets.
SQL Server Configuration Manager can be used to configure the SQL Native Client to request an encrypted connection using the Secure Sockets Layer (SSL), and to accept a self-signed certificate without validation. You can also request encryption by setting the Encrypt DBParm to 1, which sets the SQL Native Client connection string keyword Encrypt. To enable encryption to be used when a certificate has not been provided on the server, set both Encrypt=1 and TrustServerCertificate=1. The value of TrustServerCertificate is ignored if Encrypt is not set to 1.
Examples
To specify that PowerBuilder should encrypt data:
-
Database profile
Select the Encrypt Data check box on the System page in the Database Profile Setup dialog box.
-
Application
Type the following in code:
SQLCA.DBParm="Encrypt=1"
Or
SQLCA.DBParm="Encrypt='True'"
See also